OWASP Vulnerable Web Applications
Salimos a la caza y captura de aplicaciones web vulnerables, que han sido preparadas a propósito para entrenar y practicar los conocimientos de seguridad que vamos adquiriendo.

Salimos a la caza y captura de aplicaciones web vulnerables, que han sido preparadas a propósito para entrenar y practicar los conocimientos de seguridad que vamos adquiriendo.

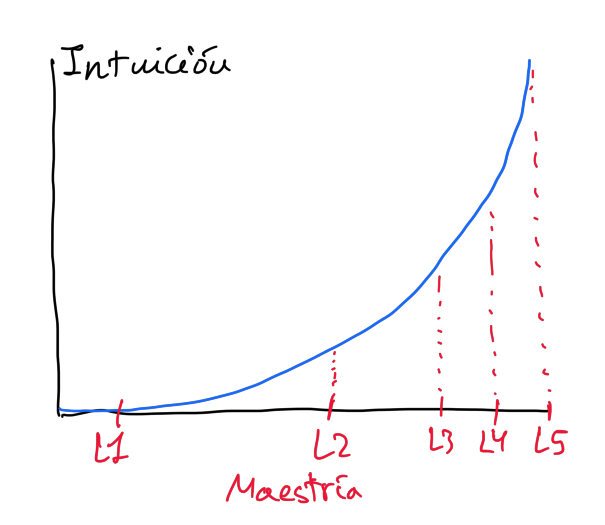
Resumen de las etapas que Stuart E. Dreyfus describe en su artículo de 2004, las cuales acompaño con ejemplos de mi día a día en desarrollo, testing y gestión.
As a dev we are responsible in delivering value over number of lines of code, that is our focus. Do not develop a tool from zero when there are tons of them out there that cover your needs.

Hearing the word "creative" is usually associated to design environments, but being creative is not limited to a specific context thus everyone can be creative in their own personal an profesional life.

10 years has passed since its launch and it continues to be a highly reliable NoSQL database service that fits in almost every scenario.

We are going to mention the most important tools out there to measure Core Wb Vitals.
My experience about the transition from individual contributor to manager.

A basic explanation about what Growth Hacking is, how it is related to the development ecosystem, and our role as developers.

If you daily meetings are not working properly, do not look for solutions in articles all over the internet, you may be able to find them in the members of your team.

My own endpoint which will receive an IP as query parameter and it will return location info such as country and city
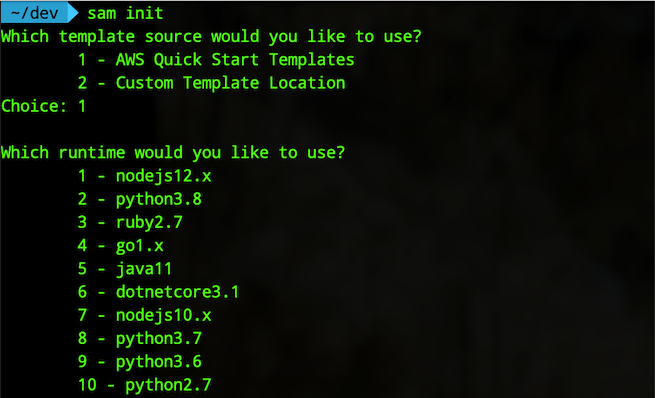
My own endpoint which will receive an IP as query parameter and it will return location info such as country and city
